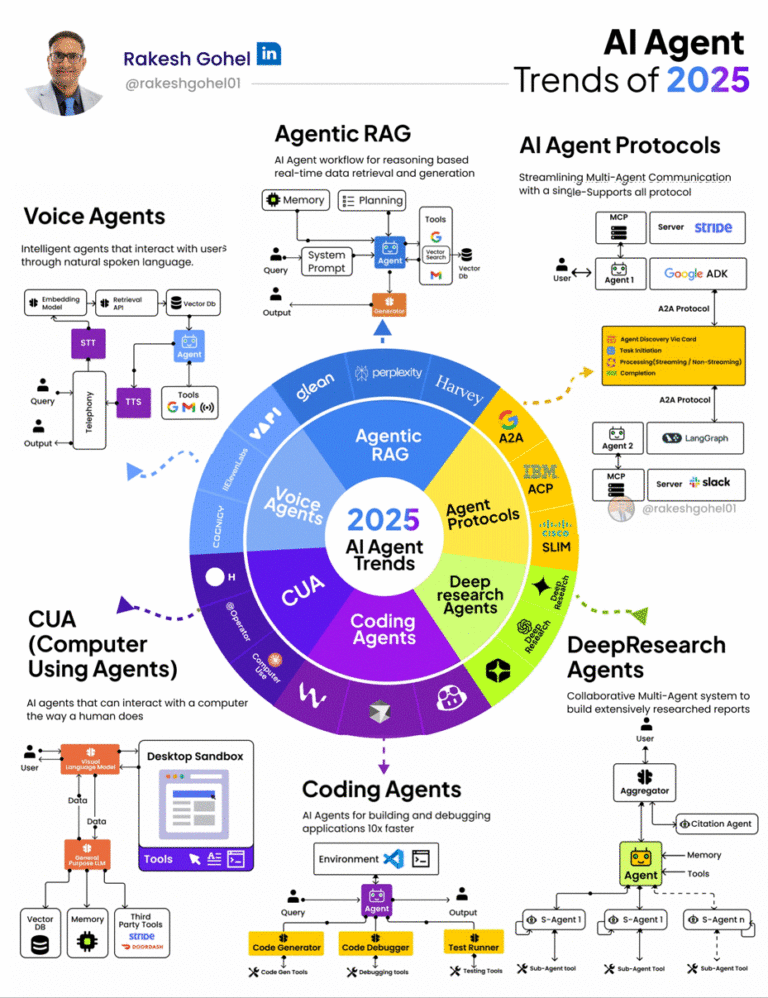
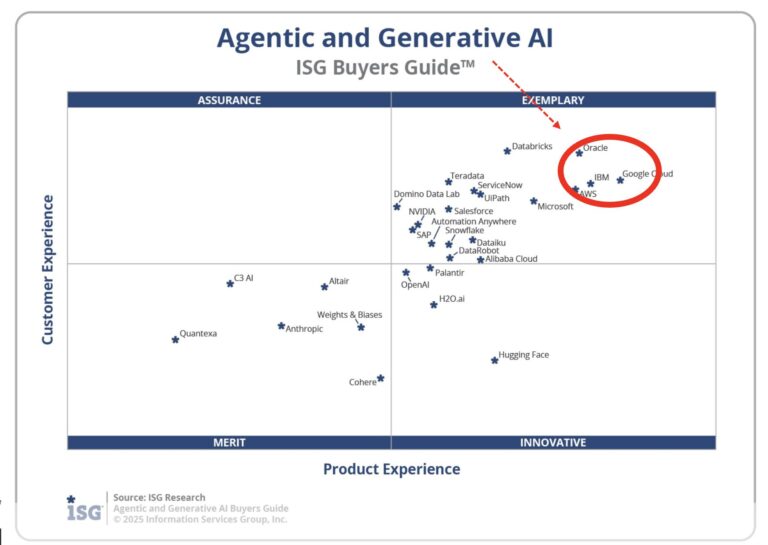
When an organization uses artificial intelligence, it means handling data in new and complex ways. Policy exists to protect data while keeping AI systems running smoothly. This might seem overwhelming at first, but to simplify:
Start with three basic questions:
- What data do your AI systems use?
- Who needs to access it?
- How will you protect it?
A good policy should answer these questions clearly. Focus on:
Data Protection
- Label what needs protecting
- Control who sees it
- Track where it goes
Security
- Set basic safeguards
- Watch for problems
- Establish a documented procedure of what to do if something goes wrong
Privacy
- Inform users what you’re doing
- Respond to their requests
- Engender their trust
The key is starting with what matters most and what you can actually implement today. Here we present 2 examples:
Example 1: Hospital AI Diagnostic Assistant Policy for Data Privacy and Security
This hospital will use artificial intelligence to assist in the analysis of medical images and patient records. The following policy establishes mandatory requirements for protecting all patient data processed by these AI systems.
Protected Data
All patient data processed by our AI diagnostic systems is classified as Protected Health Information (PHI) under HIPAA regulations. Protected data includes medical imaging files, laboratory test results, patient diagnostic histories, and any outputs generated by AI analysis systems.
Access Control Requirements
Licensed physicians actively assigned to patient care are authorized to access AI diagnostic outputs through their clinical workstations. All system access requires dual-factor authentication which must be renewed every eight hours. Information Technology (IT) staff performing system maintenance must use designated Privileged Access Workstations that are technically prevented from accessing patient records. The system automatically logs every access attempt including the user identifier, timestamp, and access location.
Data Protection Measures
Patient data must remain within the secure Epic medical records environment at all times. AI analysis operations will run exclusively in an isolated HIPAA-compliant processing environment. System logs will be retained for seven years, with mandatory audits conducted on the first Tuesday of each month. The system will automatically lock any account that exceeds three failed access attempts within a sixty-minute period.
Security Incident Response
Security incidents are classified and handled according to severity:
- Severity Level 1 incidents involving potential data breaches must be reported to the Privacy Officer within one hour of detection.
- Severity Level 2 incidents involving unauthorized access attempts must be reported to the Security Officer within four hours of detection.
- Severity Level 3 incidents involving system anomalies must be reported to IT Operations within twenty-four hours of detection.
All security incidents require detailed written documentation submitted to the Security Office within forty-eight hours of the initial report.
Patient Rights and Notifications
All patients will receive written notification of AI diagnostic system usage during their intake process. The hospital must fulfill patient requests for AI analysis records within fifteen business days of receipt. Patients maintain the right to opt-out of AI diagnostic assistance by submitting written notice. The hospital will process all opt-out requests within two business days of receipt.
Example 2: Financial Trading AI Policy for Data Privacy and Security
This investment firm employs artificial intelligence systems to analyze market data and assist in trading decisions. This policy establishes mandatory requirements for protecting client and market data processed through these AI systems.
Protected Data Categories
All data processed by our AI trading systems is classified into one of two protection tiers. Tier 1 encompasses client portfolio data, trading strategies, and position information. Tier 2 encompasses market analysis data, historical trading patterns, and aggregated performance metrics. Both tiers require strict controls as detailed in this policy.
Access Control Requirements
Trading system access is restricted to licensed financial advisors and authorized algorithmic trading specialists. All system access requires hardware security key authentication combined with biometric verification, with credentials that expire every four hours. System administrators must use dedicated secure workstations connected through our private trading network. The system maintains comprehensive access logs including user identification, timestamp, location, and specific data elements accessed.
Data Protection Measures
All client data must remain within our secure trading environment. AI analysis operates in an isolated computational environment with no external network access (air gap). The system maintains full audit logs for ten years as required by SEC regulations. Daily backup snapshots are encrypted and stored in geographically dispersed secure facilities. When a system detects ten failed access attempts within a thirty-minute window it will initiate an automatic trading halt.
Security Incident Response
The following security incidents require immediate response:
- Data breaches affecting client information must be reported to the Chief Compliance Officer within thirty minutes of detection.
- Unauthorized trading pattern anomalies must be reported to the Risk Officer within sixty minutes of detection.
- System performance irregularities must be reported to Trading Operations within two hours of detection.
All security incidents require a detailed incident report submitted to the Compliance Department within twenty-four hours of resolution.
Client Rights and Notifications
All clients receive detailed documentation of AI trading system usage during account opening. The firm must respond to client data requests within ten business days of receipt. Clients maintain the right to opt-out of AI-assisted trading through written instruction. The firm will implement all trading preference changes within one business day of receipt.